

Seconize DeRisk Centre – Part 1
Risk-Based Vulnerability Management Sneak Peek for CISOs
(This blog is Part 1 of three-part series)
With the advancements in technology and with every business relying heavily on cloud solutions, software solutions, and cyber solutions to grow their business, Cyber Risk Management has become a non-negotiable part of any business’s strategy.
Yet, CISOs from both large and small organizations, find it extremely challenging to understand and mitigate these cyber risks. The root cause of this problem is that cyber attacks are becoming more frequent than ever.
According to a survey, cyber-attacks caused damages worth $6 trillion USD globally in 2021 and it is expected to grow by 15 percent per year over the next five years, reaching $10.5 trillion USD annually by 2025.
It, therefore, becomes imperative for your company’s cybersecurity strategy to be more proactive than reactive.
If you want to learn more about cybersecurity risks, how to identify them and how to mitigate them, then read on.
Seconize DeRisk Centre (DRC) is an end-to-end security solution for identifying and managing risks that enables CISOs to quickly visualize Security Posture and track remediation across Applications, Cloud, and Infrastructure all within a few clicks.
The all-new DRC is built to answer the following questions and represents the findings via its Security Posture Dashboards.
What is at risk?
The first step in protecting your organization’s assets against cyberattacks is understanding what are the different assets that are at risk.
There are many things that can be at risk when it comes to cyberattacks. This can include personal information, financial information, and even business secrets. It’s important to identify what is at risk so that you can take steps to protect yourself and your organization.
Some of the most common things that are at risk include:
Personal information: This can include your name, address, Social Security number, and other sensitive information. If this information falls into the wrong hands, it could be used for identity theft or other fraud.
Financial information: This can include your credit card numbers, bank account numbers, and other financial details. If this information is stolen, it could be used to make unauthorized charges or withdrawals.
Business secrets: This can include trade secrets, proprietary information, and other confidential business information. If this information is leaked, it could give competitors an unfair advantage.
Network Access: This can include access to physical servers that store data, as well as the software and databases that run on them. If these assets are compromised, it could lead to data breaches or other disruptions.
To protect your organization’s assets, you need to know your IT asset landscape and the impact of the risk on your day-to-day functioning as well as its impact on your clients’ infrastructure and assets.
Some of the factors to consider are given below.
- Will a data breach likely result in the loss of your Customer Data or Intellectual Property?
- Will downtime due to ransomware likely cause disruption of your revenue-generating services? Or disrupts internal operations and employee productivity?
- What will be the impact of your disruption or downtime on your client’s operations and functioning?
The question then arises is that do you have the complete inventory of your IT infrastructure assets and have you categorized them based on the risk they pose. Do you know which are high-risk assets and which customer data or intellectual property is most vulnerable to cyber-attacks?
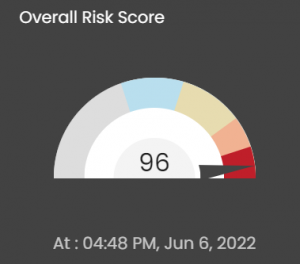 Seconize DeRisk Centre provides visibility into Asset-Based Risk scores and aggregated risk scores across all the IT Assets (or any subset of them).
Seconize DeRisk Centre provides visibility into Asset-Based Risk scores and aggregated risk scores across all the IT Assets (or any subset of them).
This visual representation makes it easy for you, as the decision-maker to become aware of your assets based on how high-risk or low-risk they are and therefore helping you to make wise decisions according to their respective risk scores.
Why is it at risk?
Once you have identified which of your physical or information or software assets are at risk, the next step is to understand what vulnerabilities exist in your systems, which when exploited by cyber attackers could impose a threat to your infrastructure.
These vulnerabilities are not just loopholes in software applications, but they could also be human errors, for example, misconfiguration of applications, not enabling the highest security standards in applications, etc.
Addressing these vulnerabilities could reduce the risk exposure and possibility of cyber attacks. That is where Seconize DeRisk Centre comes to your rescue.

Seconize DeRisk Centre gives visibility into active vulnerabilities across all the IT Assets and prioritizes the vulnerabilities based on the risk it poses to the organization.
This enables better decision-making and optimizing the effort in de-risking as well as creating risk mitigation measures.
Who is working on it?
After you have identified the risk and identified the vulnerabilities leading to the risk, it is now time to understand what is being done to address those risks.
Typical questions that need to be answered are:
- Are the RACI Matrix in place to know who is Responsible, Accountable, Consulted, and Informed for each type of vulnerability?
- Are all the respective stakeholders (IT asset owners, Application Engineers, and Administrators) informed?
- Are there expectations set on response times for Critical, High, Medium, and Low issues?
- Are the deadlines being met?
Seconize DeRisk Centre helps you do all the above and more.
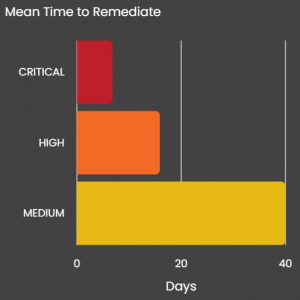 Seconize DeRisk Centre provides visibility into remediation efforts of all stakeholders, Mean-Time-To-Remediate, and track Service Level Agreements( SLAs) on risk remediation and meet regulatory, and compliance requirements.
Seconize DeRisk Centre provides visibility into remediation efforts of all stakeholders, Mean-Time-To-Remediate, and track Service Level Agreements( SLAs) on risk remediation and meet regulatory, and compliance requirements.
Subsequently, you can learn about how Seconize DeRisk Centre can help you in Risk Prioritization (Part-2) and Administration (Part – 3).














Recent Comments