

Seconize DeRisk Centre – Part 3
Risk-Based Vulnerability Management Sneak Peek for IT Administrators
(This blog is Part-3 of three-part series)
IT Administrators have a big responsibility when it comes to cyberattacks and cybersecurity. They are responsible for keeping our networks safe and secure from attack. Cyberattacks can come in many forms, so it is important for IT Administrators to be prepared for anything. There are many different types of cyberattacks, but some of the most common include:
Denial of Service (DoS) Attacks: DoS attacks are designed to overload a system with traffic, preventing legitimate users from accessing it.
Phishing Attacks: Phishing attacks involve trying to trick users into giving up sensitive information, such as passwords or credit card numbers.
Malware Attacks: Malware attacks are designed to install malicious software on a system in order to steal data or cause damage.
IT Administrators play a vital role in protecting our networks from these cyberattacks. They are responsible for keeping our systems up to date with the latest security patches, and they also monitor network traffic for any suspicious activity. If they see something suspicious, they can take steps to block the attack and protect our data.
This is where Seconize DeRisk Centre (DRC) becomes a vital tool for all IT Administrators.
Seconize DeRisk Centre (DRC) enables IT Administrators to onboard IT Assets across Applications, Cloud, and Infrastructure for continuous vulnerability and misconfiguration assessments.
The all-new Seconize DRC is simplified for
- Onboarding Users
- Inventorying Assets
- Integrating with Connectors
- Scheduled Jobs
This helps IT, Administrators, in identifying their attack surface (both external and internal) and subsequently help security analysts to identify and mitigate the likely impact of cyber-attacks.
Onboard Users
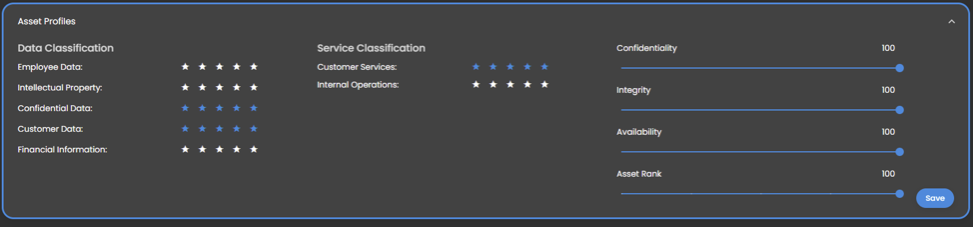
 Seconize DeRisk Centre provides a simple User Management functionality. Being the only unified vulnerability management product across Applications, Cloud and Infrastructure, Users can be provided granular privileges for all the product capabilities.
Seconize DeRisk Centre provides a simple User Management functionality. Being the only unified vulnerability management product across Applications, Cloud and Infrastructure, Users can be provided granular privileges for all the product capabilities.
Also, they can be restricted to their respective “asset scope”. This ensures that the least privileged access can be provided to the Users.
Inventory Assets
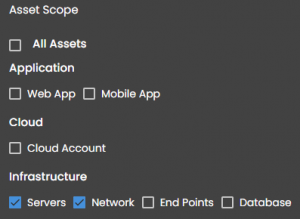
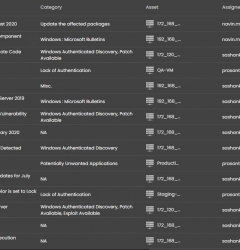
IT environments are complex and continuously evolving to meet business needs. The most comprehensive asset inventory is needed for identifying the attack surface continuously.
Seconize DeRisk Centre provides a variety of ways to ingest the assets.
- Automatic discovery of External facing Web and Mobile Applications
- Automatic discovery of Cloud Assets via REST APIs
- Import via Spreadsheets
- Simple workflow to create individual assets
- Integration with CMDB tools.
Subsequently, asset classification is important for identifying the crown jewels and modeling the impact of cyber-attacks.
All the assets can be grouped based on homogenous properties (such as asset type or sub type) or heterogenous properties (such as business unit, location, department), or any other custom criteria.
Integrate with Connectors
Often a variety of tools like CMDB, Cloud Services, and Third Party Scanners are deployed for accomplishing different IT needs.
Seconize DeRisk Centre comes with numerous connectors that integrate with IT Infrastructure like:
- Asset Management tools like Manage Engine
- Identity Management tools like Azure AD
- Cloud Services like AWS, Azure, GCP
- Third-Party Commercial Scanners like Qualys, Nessus (Tenable)
- Open-Source Scanners like ZAP
- Ticketing Systems like JIRA
- Threat Intelligence Sources that support STIX/TAXII or custom REST APIs
Scheduled Jobs
 With the ever-changing threat landscape, it is important to adopt a product that helps you automate and achieve continuous vulnerability assessments.
With the ever-changing threat landscape, it is important to adopt a product that helps you automate and achieve continuous vulnerability assessments.
Seconize DeRisk Centre comes with a powerful scheduling engine to automate both continuous assessments and continuous remediation.
Continuous Assessment Jobs
- Active Scans are either aggressive or authenticated (or both) scans depending upon the target asset type
- Passive Scans are gentle and often do not cause excessive load on the target assets.
- Discover Scans identify the asset (and respective services) footprint either using inbuilt algorithms or via Connectors.
Continuous Remediation Jobs
- Manual Remediation: Automated Ingestion of vulnerabilities into JIRA (or other ticketing systems)
- Automated Remediation: Automated Policy enforcements to mitigate Cloud Misconfigurations
Seconize offers advanced manual penetration testing to complement and cover the business logic and proprietary test scenarios for all its customers as part of all our offerings.
This is the last blog post in this series to learn about Seconize DeRisk Centre.
Other blogs in this series can be found here (Part – 1), (Part – 2).













Recent Comments