

Understanding CERT-In’s Comprehensive Cyber Security Audit Policy Guidelines (2025): What Organizations Must Know
Note: This blog is issued under public interest On July 25, 2025, the Indian Computer Emergency Response Team (CERT-In) released the CERT-In’s Comprehensive Cyber Security Audit Policy Guidelines (Version 1.0) — a structured and standardized audit framework that is mandatory

Extension towards Adoption and Implementation of Cybersecurity and Cyber Resilience Framework (CSCRF) for SEBI Regulated Entities (REs)
CIRCULAR SEBI/HO/ ITD-1/ITD_CSC_EXT/P/CIR/2025/96 June 30, 2025 To, All Alternative Investment Funds (AIFs) All Bankers to an Issue (BTI) and Self-Certified Syndicate Banks (SCSBs) All Clearing Corporations All Collective Investment Schemes (CIS) All Credit Rating Agencies (CRAs) All Custodians All
Seconize Researchers Discover and Responsibly Disclose Critical IRCTC Vulnerability Exposing User Data
Bengaluru, India – June 19, 2025 – Cybersecurity researchers at Seconize, a leading provider of cyber risk and compliance automation solutions, have responsibly disclosed a significant security vulnerability in the Indian Railway Catering and Tourism Corporation (IRCTC) platform, which exposed
Seconize Researchers Uncover and Help Fix IRCTC Vulnerability
IRCTC Vulnerability: Introduction Note – A big shoutout to Rohan Kar, one of our security researchers at Seconize, for identifying a critical flaw in the IRCTC platform In June 2025, while booking a train ticket via the official IRCTC platform, I came

The Vulnerability Management Trilemma: Which Path Will You Take?
Like the proverbial pond teeming with fish and the lurking fisherman, our digital environments are rich with valuable data, and malicious actors are always on the hunt. Just as the ancient Panchatantra told the tale of three fish with vastly

FAQs on Cybersecurity and Cyber Resilience Framework (CSCRF) for SEBI REs and Framework for Adoption of Cloud Services by SEBI REs
Frequently Asked Questions (FAQs) on Cybersecurity and Cyber Resilience Framework (CSCRF) for SEBI REs and Framework for Adoption of Cloud Services by SEBI REs These FAQs aim to address the most common queries/ questions SEBI REs have about the CSCRF
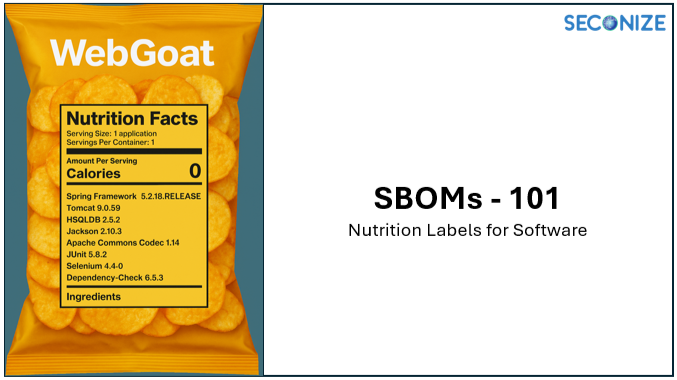
SBOMs 101: The Beginner’s Guide to Software Nutrition Labels
Cyber risks have become a significant concern for organizations worldwide. These risks come in various forms and can originate from multiple sources. Broadly, cyber risks can be categorized into three main types: Technical Vulnerabilities, Process/Policy Gaps, and Third-Party Risks. Understanding

Understanding and Managing Different Types of Cyber Risks
Cyber risks have become a significant concern for organizations worldwide. These risks come in various forms and can originate from multiple sources. Broadly, cyber risks can be categorized into three main types: Technical Vulnerabilities, Process/Policy Gaps, and Third-Party Risks. Understanding

Seconize DeRisk Centre – Part 2
Seconize DeRisk Centre – Part 2 Risk-Based Vulnerability Management sneak peek for Security Analysts (This blog is Part 2 of three-part series) As the world increasingly moves online, cyberattacks are becoming more and more common. That’s where security analysts come

What’s the ROI of Our Cybersecurity Investments?
In order to determine if the investments we make in cybersecurity are worthwhile, we need to consider several key factors, including risk management, ROI, and the potential impact of a cybersecurity incident on the organizational infrastructure and assets.


Recent Comments