

Like the proverbial pond teeming with fish and the lurking fisherman, our digital environments are rich with valuable data, and malicious actors are always on the hunt. Just as the ancient Panchatantra told the tale of three fish with vastly different approaches to a looming danger, modern vulnerability management presents us with a similar trilemma. Which fish are you?
The First Fish: Viveka – Secure by Design and Proactive Prevention
Viveka, meaning wisdom and foresight, represents the pinnacle of modern vulnerability management: building systems that are secure by design. This isn’t a reactive measure; it’s a fundamental philosophy woven into the very fabric of development and deployment.
Think of Viveka as the architect who meticulously plans every aspect of the pond, ensuring strong natural defenses, hidden escape routes, and a clear understanding of potential threats before they even materialize.
In the context of modern vulnerability management, this translates to:
- Secure Coding Principles: Developers are trained in and actively implement secure coding practices, minimizing the introduction of vulnerabilities from the outset. This includes adhering to OWASP Top Ten guidelines, performing thorough code reviews, and utilizing static and dynamic application security testing (SAST/DAST) early in the development lifecycle.
- Security Champions: Dedicated security champions are embedded within development teams, fostering a security-first culture and ensuring that security considerations are integrated into every stage.
- Threat Modeling: Proactively identifying potential threats and vulnerabilities in the design phase, allowing for mitigation strategies to be implemented before code is even written.
- Secure Configuration Management: Establishing and maintaining secure configurations for all systems and applications, reducing the attack surface.
- Immutable Infrastructure: Deploying infrastructure as code, making changes controlled and auditable, and reducing the risk of configuration drift and vulnerabilities.
- Security Training and Awareness: Educating all personnel on security best practices to prevent human error, a significant source of vulnerabilities.
Organizations that embody the “Viveka” approach understand that prevention is far more effective and cost-efficient than remediation. They invest in building resilient systems from the ground up, significantly reducing their exposure to vulnerabilities and potential breaches.
The Second Fish: Yukti – Regular Scanning and Diligent Management
Yukti, meaning strategy and cleverness, represents the more common approach: regular vulnerability scanning and diligent management. This organization acknowledges the inherent complexities of modern systems and understands that vulnerabilities will inevitably arise. Their strategy is to actively seek out these weaknesses and address them promptly.
Think of Yukti as the intelligent fish who, while living in the same pond, understands the fisherman’s threat. It doesn’t leave preemptively but remains vigilant, constantly scanning for the tell-tale signs of the net and devising clever escape plans.
In modern vulnerability management, this looks like:
- Regular Vulnerability Scanning: Implementing automated and manual scanning tools to identify known vulnerabilities in infrastructure, applications, and dependencies. This includes network scans, web application scans, and container image scans.
- Vulnerability Assessment: Analyzing scan results to understand the context, severity, and potential impact of identified vulnerabilities.
- Prioritization and Remediation: Establishing clear processes for prioritizing vulnerabilities based on risk and implementing timely remediation efforts, including patching, configuration changes, or code fixes.
- Vulnerability Management Platform: Utilizing a centralized platform to track vulnerabilities, assign remediation tasks, and monitor progress.
- Patch Management: Implementing a robust patch management process to ensure timely application of security updates.
- Security Audits and Penetration Testing: Conducting periodic security audits and penetration tests to proactively identify weaknesses that automated scans might miss.
Organizations following the “Yukti” approach are actively managing their risk. They understand that continuous monitoring and timely action are crucial to minimizing the window of opportunity for attackers. While they may still experience vulnerabilities, their proactive approach significantly reduces the likelihood and impact of a successful breach.
The Third Fish: Aalas – Ignorance and Inaction
Aalas, meaning laziness and indolence, represents the dangerous approach of doing nothing and hoping for the best. This organization either lacks awareness of the threat or chooses to ignore it, believing they are somehow immune.
Think of Aalas as the complacent fish who dismisses the fisherman’s warnings, believing that fate will protect them. They continue to swim obliviously, unaware of the impending danger until it’s too late.
In the context of modern vulnerability management, this translates to:
- Lack of Regular Scanning: Not implementing or inconsistently running vulnerability scans.
- Ignoring Vulnerability Reports: Failing to address or even acknowledge identified vulnerabilities.
- Outdated Systems and Software: Running unsupported or unpatched systems and applications.
- Absence of Security Awareness: A lack of security training and awareness among employees, leading to risky behaviors.
- No Incident Response Plan: Being unprepared to handle a security breach when it inevitably occurs.
Organizations that embody the “Aalas” approach are playing a dangerous game of chance. In today’s threat landscape, inaction is a virtual invitation for attackers. The consequences of a breach can be devastating, leading to financial losses, reputational damage, legal liabilities, and the erosion of customer trust.
Which Fish Will You Be?
The story of the three fish serves as a timeless allegory for how we approach challenges. In the realm of modern vulnerability management, the choice is clear.
- Will you be Viveka, investing in building a secure foundation and proactively preventing vulnerabilities?
- Will you be Yukti, diligently scanning and strategically managing the inevitable weaknesses in your systems?
- Or will you be Aalas, burying your head in the sand and hoping that the fisherman’s net somehow passes you by?
The digital pond is becoming increasingly treacherous. Choosing the path of Viveka or Yukti is not just a matter of best practice; it’s a necessity for survival in the modern threat landscape. Ignoring the risks and adopting the approach of Aalas is a gamble that no organization can afford to take. The question isn’t if you will be targeted, but when. Prepare accordingly, choose wisely, and ensure you’re not the third fish in this modern-day tale.
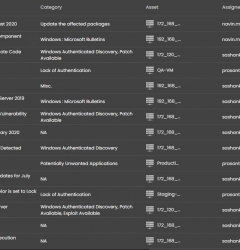
Seconize DeRisk Center enables you to manage the complete life cycle of vulnerabilities. Book a demonow !






Recent Comments