

Introduction
It is important for any company to have cybersecurity in place, no matter the industry. Cyber threats are increasing at an alarming rate, which means that cybersecurity should be a top priority for any business.
So, how does one ensure that their digital assets, infrastructure, applications are protected from all ends?
There are two ways to go about this:
- Cyber security as a service along with needed consultancy
- Cyber Security with the product, a SaaS-based one along with need-basis consultancy
It’s difficult to know which is best without giving it some thought beforehand.
This post will outline the pros and cons of each option so you can make your decision more wisely.
But before we get into the solution part, let us first analyze the cyber risks that you are currently facing or could be potentially dealing with.
Cyber risks to your digital assets
Cyber risks are those yet to materialize events that could potentially impact an organization’s digital assets, applications, and infrastructure.
The disruption to your service, your financial system, your business could happen in many forms.
Let’s discuss those in detail in this section.
Disruption of Business
Disrupting your business is a powerful way for hackers to gain access to your infrastructure and render your business non-functional.
It’s one of their favorite tactics as it can cause a lot of damage in a short period.
Cybercriminals can also disrupt your business with ransomware attacks, which have increased in popularity over recent years.
The goal is usually to extort money from the company or steal confidential data that they can use for financial gain.
One example of this occurred in 2017 when ransomware called WannaCry infected computers around the world.
This attack was particularly scary for two reasons: firstly, it targeted old Windows systems that were no longer supported by Microsoft, and secondly, it used the EternalBlue exploit to spread across networks quickly.
Disruption of Data
The data of any business is its highest valuable asset. This data could be confidential information of the business’s clients, vendors, employees, or it could be intelligence that the business has gathered by spending millions of dollars.
It could also include intellectual property, patents, or proprietary software that the company has developed.
These are all very valuable assets to any organization and their loss can be potentially devastating for an organization’s long-term prospects.
Any cybersecurity attack on your infrastructure (systems, applications, etc.) is a direct threat to these data assets of yours as they might get compromised, stolen, or destroyed. Hackers have a lot of options when it comes to data theft including:
Phishing Attack
A scam designed to get users’ confidential information such as passwords and credit card details by pretending that the site is legitimate while asking for them in an email.
Brute Force Attacks
This is a technique where hackers try to guess your passwords by trying different combinations until they find the right one.
Social Engineering
This is a technique where attackers use human psychology to exploit people’s trust and get them to reveal confidential information such as passwords or log-in credentials.
Malware
This is software that is designed to damage or disable a computer, smartphone, or another device.
Hackers can use one of these techniques to gain access to confidential company assets such as intellectual property, financial information, business plans, etc., which could cause significant damage to your business.
Risk Mitigation Strategies
All the risks listed above and many more risks that are not mentioned in this article pose a real threat to any organization, big or small, belonging to any industry.
For these risks, we must discuss the risk mitigation strategies that will counter the hackers and cyber-attacks in the best possible way.
Now cyber security is a very dynamic field and not all companies can afford to have resources internally to drive the cyber security program.
The option companies have been using is to have a small internal team heading cyber security programs and use external help.
With respect to external help, there are 2 ways to approach this.
- Cyber security as a service along with needed consultancy
- Cyber Security with the product, a SaaS-based one along with consultancy
In the rest of the article, we will explore the pros & cons of each of these approaches and which one your company can focus on.
Cybersecurity management with a cybersecurity service vendor
You might consider outsourcing cybersecurity management to a third-party service company and letting them manage your infrastructure and your systems.
Following are the pros and cons of outsourcing cybersecurity
Benefits of having a cyber security service vendor
Cyber security as a service is a proven model and has traditionally been tried by every business.
Let’s explore how some of the key benefits of having cyber security as a service-based solution.
Immediate Access To Expertise
The major benefit of hiring external cybersecurity experts is that you get access to their expertise immediately. These experts have years of experience in dealing with different types of cybersecurity threats and they know how to deal with them effectively.
They also keep up with the latest security trends and developments so they can provide you with the best possible protection against all current and future threats.
Centralized Management
Another major benefit of outsourcing cybersecurity is that you can centralize cybersecurity management and report. This means that everything related to cybersecurity will be handled by the cybersecurity experts at your service provider, so there won’t be any confusion or lack of transparency when it comes to cybersecurity in the organization.
You will also get regular reports on incidents, threats, and vulnerabilities so you can always keep track of the cybersecurity posture of your organization.
Consistent And Proven Solution
When you outsource cybersecurity, you are getting a proven and consistent solution that has been tested and optimized by the service provider. This means that you don’t have to worry about the security of your infrastructure which has been there and done that for many other organizations.
Disadvantages of cyber security service providers
Though there are obvious benefits of relying on 3rd party vendors, consultancy to avail cyber security service, it does come with some serious consequences.
High costs of outsourcing cyber security as a service
Firstly, Hiring cybersecurity experts can be very pricey and it is unlikely that your organization will have the budget to pay them regularly.
You might also need to invest in hiring cybersecurity consultants who can help you build or maintain a secure infrastructure from scratch, which would add up costs even more. To cut the huge expense, most businesses end up taking partial service or getting service a few times in a year.
Lacks continuous service
Secondly, due to the above issue cyber security service offered at few intervals in a month or quarter, another drawback of cybersecurity outsourcing you must consider.
Now cyber threats aren’t discrete like this. They can come anytime.
Lack of continuous security management means the chances of not being able to prevent threats with their processes or anything interfering with their ability to protect your cybersecurity infrastructure is very high.
Service-based organizations rarely use a data-driven approach which limits them to preempt remedial solutions. They are mostly reactive
Long-term commitment
Finally, Hiring cybersecurity experts can be a long process and you will have to make sure that the candidates meet your specific requirements as well as those of cybersecurity standards before making them part of your team.
Once you do, they will work to protect your cybersecurity infrastructure and systems 24/365. They might also work on multiple projects at once so there is always a chance that their attention may be divided between the cybersecurity of your organization and that of other clients.
Managing cyber security with product-based solution
Instead of outsourcing cybersecurity to a third-party service-based company, you could consider using cybersecurity products to secure your assets and infrastructure.
Cyber security product solutions are cloud-based and work on the SaaS model.
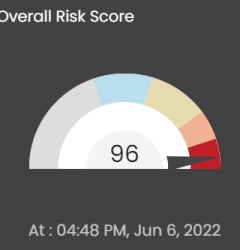
At Secognize, we have built an All In One Platform called Seconize DeRisk Center, which once set up monitors your network your infrastructure, your assets, and applications and generates notifications when action is needed.
It helps your organization understand your security posture and exposure resulting from your digital assets. You can allocate resources accordingly by following the prioritized recommendations thereby ensuring compliance.
This is a continuous risk and compliance management solution that protects your assets, infra, and applications 24×7.
The products are developed with holistic risk assessment capability to address all asset types of the company and provide a unified view.
The product becomes an intelligence partner you need to ensure your end-to-end infrastructure security and asset protection.
Having said that, the followings are the pros and cons of using cybersecurity products.
Advantage of using cyber security products to secure
Let us explore some of the key advantages the cyber security teams, as well as businesses, get using cloud-based, saas products.
Products are less expensive over the long term
Though deploying products in beginning might require certain investments, over the long term say 1-3 years, cybersecurity products turn out to be less expensive.
This is because inherently saas products are designed to reduce costs to cover more assets and require less manpower to manage.
Enhanced protection from cyber threats
The cybersecurity solutions deployed are running continuously and use the risk-based model to prioritize the issues.
The product can easily add additional features, services to help you secure your organization against all types of threats and vulnerabilities just like a cybersecurity service would do but with much more reliability and consistency.
The lean security team is enough
Cyber security expert resources are expensive. With cyber security product solutions like Seconize DeRisk, you not only get their product running continuously, but they also provide on-demand consultancy.
This helps you to just maintain a lean team and achieve significant security protection
You don’t need to invest in building or maintaining a large in-house security infrastructure. This can save your organization a lot of time and money.
Increased control of your assets and infrastructure
When you use cybersecurity products instead of cybersecurity services, you are in complete control over the security of your assets and infrastructure.
Since cybersecurity products are easy to implement as well as manage, they can be done by any member of your team without having to call on an expert for help.
Disadvantages of using cyber security products
Though there are obvious advantages of cyber security product-based solutions, they may not be applicable for all companies or you must be aware of some of the pre-requisites for using these solutions.
Initial setup and learning to use product
Using cybersecurity products can be a little challenging as you will need to learn how to use them before they start working for your cybersecurity.
At Seconize, we provide clients with cybersecurity training and consulting services that help organizations get started with the product quickly and efficiently.
We not only train your people, but we ourselves are available to consult any issues if necessary.
Tech-expertise & interaction Is necessary
When using cybersecurity products instead of cybersecurity services, you will have to learn how cybersecurity products work and use them in a way that they can provide the best cybersecurity protection for your organization.
While this is not very difficult or time-consuming, it requires a certain level of tech-savvy which might be hard to find in all members of your team.
At Seconize, we solve this problem by being on call as and when needed to help your staff acquire the technical expertise and become 100% comfortable with our tools.
Shift in the approach to address cyber-security
Though this is not a disadvantage, important to mention that the internal team must rely on the product to get regular alerts, notifications and monitor for any change in risk profile, and address vulnerabilities.
It is key for the internal team to fix instead of relying on 3rd party experts
At Seconize, we solve this problem by setting up alerts and notifications that can inform the concerned authorities of any incidents that need attention.
And as a customer one can also avail consultation service, so you get the best of both the worlds
Cybersecurity Product Solution Vs Service Solution
| Area of Comparison | Product-based solution | Services-based solution |
| Speed of Implementation and Results | Products are ready to plug and play. So, you can install and configure, and your security vigilante will be up and running in no time. Therefore, results are achieved instantly. | Customizing and implementing security solutions manually will be a more time-consuming process and human error might lead to missing out on some nodes that need to be monitored. |
| Internal expertise required | When you get a product, then product installation and configuration is mostly the responsibility of the vendor and thus no internal expertise is required. | When you work with a third-party expert company that manages your cybersecurity process, they have subject matter experts for setup, configuration, and monitoring. But to manage your vendor, you need a few employees who have a basic understanding of what is going on to hold the 3rd party accountable. |
| Investment Required | The initial investment is required to buy the tool and configure the platform but later it pretty much runs on auto mode. | A recurring monthly investment is incurred to keep your infrastructure safe and secured. |
| Selection method | You see demonstrations of products and make your decision based on the offerings and your requirements. | You must vet many companies, ask for testimonials, agree on service offerings, and then make a decision. |
| Who is best served | A ready-to-use product is much better to service because it is very predictable and mature. So minimal intervention is required. | Since a third-party security company is offering its services, they are available pretty much on your beck and call. |
| Scalability | A product keeps evolving as your requirements evolve. So, scalability becomes a natural process. | Scalability means adding more resources, more members to the team, which means more cost and overhead. |
Conclusion
Protecting your company’s infrastructure and assets is the biggest responsibility of the CISO. To ensure that none of the company’s valuables are compromised, the CISO must play an active role in covering all bases.
Outsourcing the security to a third-party service company can be a workable solution until something bad happens. Then it becomes the CISO’s responsibility to clear the mess.
A platform like Seconize could give the CISO, visibility into the security of their own infrastructure, so much so that preventive and countermeasures can be implemented with ease and convenience without allowing the risks to disrupt your business functioning.
Related Post
Categories
Recent Posts
Copyright © 2024 Seconize Technologies Pvt Ltd. All rights reserved.











Recent Comments