
Seconize DeRisk Centre – Part 2
Risk-Based Vulnerability Management sneak peek for Security Analysts
(This blog is Part 2 of three-part series)
As the world increasingly moves online, cyberattacks are becoming more and more common. That’s where security analysts come in. Security analysts are responsible for identifying, prioritizing, and remediating potential vulnerabilities before they can do any damage.
In order to be successful, security analysts must have a strong understanding of both organization’s infrastructure and information security. They must be able to identify potential vulnerabilities in their infrastructure and then determine the best way to protect those systems from being exploited.
Seconize DeRisk Centre (DRC) enables Vulnerability Analysts to identify, prioritize and remediate vulnerabilities across Applications, Cloud, and Infrastructure.
The all-new DRC is simplified to identify, prioritize, and remediate vulnerabilities.
This helps Application Engineers, Cloud, and IT Administrators in mitigating the likely impact of cyber-attacks.
Identify Vulnerabilities
IT environments are complex and continuously evolving to meet business needs.
As cyberattacks become more sophisticated, it’s imperative that businesses take steps to identify vulnerabilities within their systems. We recommend conducting regular audits and assessments to ensure that your organization is aware of potential risks. By identifying vulnerabilities, you can take steps to mitigate them and protect your business from cyberattacks.
Timely identification and mitigation of issues that can likely have a devastating impact on your business are a must in today’s times.
Additionally, it’s important to have a strong cyber incident response plan in place in the event that an attack does occur. By being prepared, you can minimize the damage and get your business back up and running as quickly as possible.
Following are some areas that are more susceptible to cyber attacks than others:
- Vulnerabilities in your Windows Servers or Linux Virtual Machines
- Misconfigurations in Web and Mobile Applications
- Misconfigurations in Cloud Accounts (like AWS, Azure, GCP)
- Insecure Interfaces and APIs
- Unpatched Software
- Lack of proper security controls
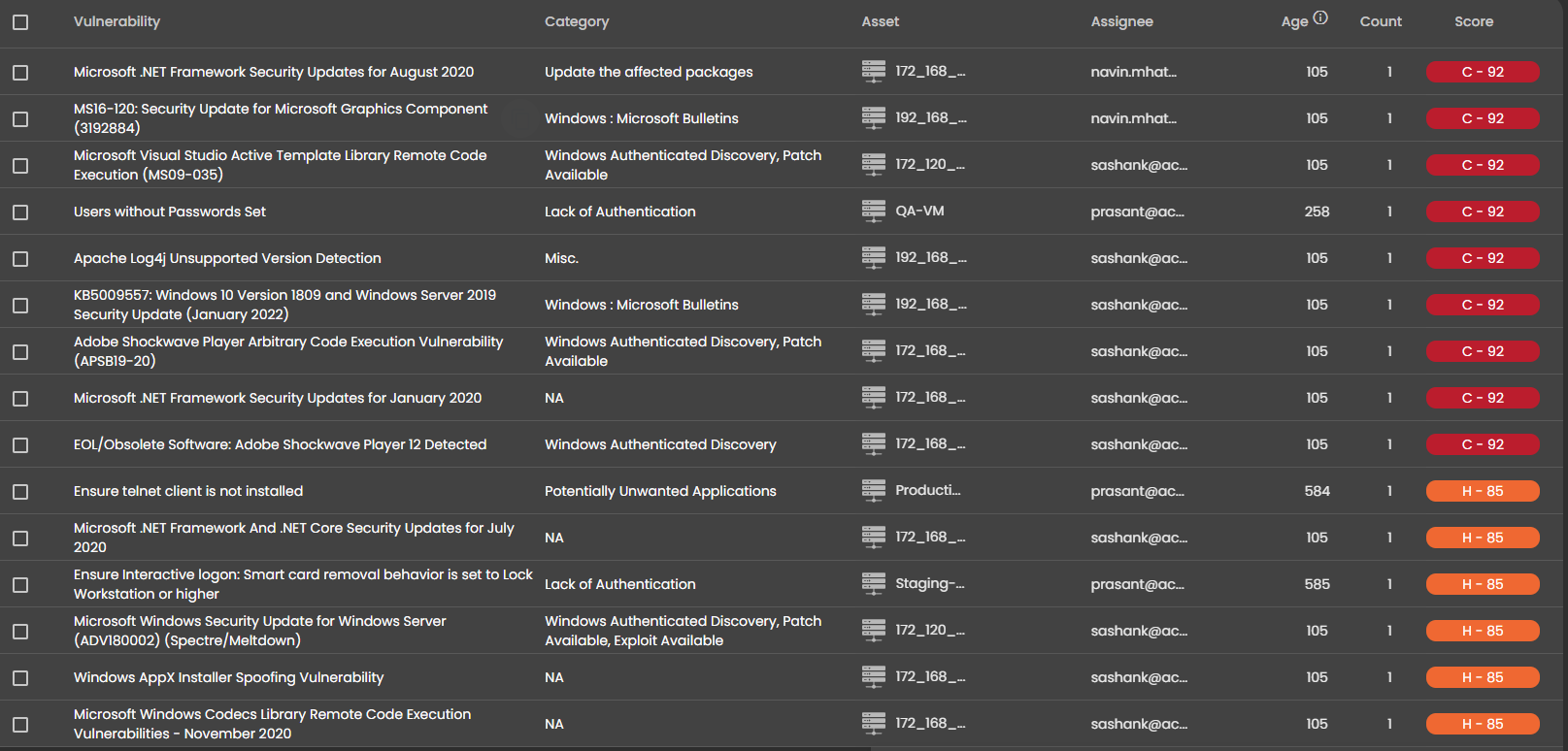
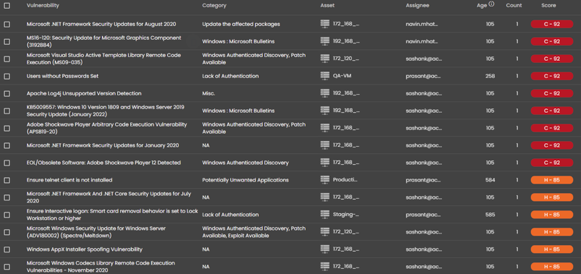
This is where Seconize DeRisk Centre, makes your job as a Security Analyst easier.
Seconize DeRisk Centre provides you clear visibility into these issues, their root cause, solution guidance, and potential impact. All the identified vulnerabilities are enriched, contextualized, and customized automatically based on your business context. This is done using expert-driven rules and advanced AI/ML Algorithms.
Risk-Based Prioritization
When it comes to cybersecurity, one size does not fit all. Organizations have different cyber risks based on their size, industry, and the type of data they possess. As a result, it’s important to prioritize cyberattacks based on the level of risk they pose.
This is where risk-based prioritization comes in. By considering the potential consequences of an attack, organizations can better assess which attacks pose the greatest threat and allocate resources accordingly.
Risk-based prioritization has taken on new importance in the wake of the recent increase in the number of cyberattacks. In the past, many organizations have been guilty of taking a “spray and pray” approach to cybersecurity, trying to protect everything equally. However, this is no longer feasible in the face of increasingly sophisticated and targeted attacks.
By prioritizing cyber risks, organizations can better protect themselves against the most serious threats. In the process, they can also save time and resources that would otherwise be wasted on less critical risks.
Given that IT assets and their respective vulnerabilities can run into thousands or more depending on the complexity of the infrastructure, prioritization becomes of utmost importance for remediating them.
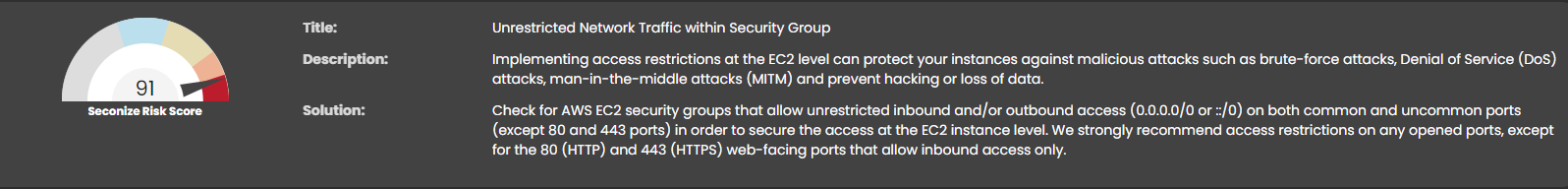
Seconize DeRisk Centre prioritizes all the identified vulnerabilities using advanced decision algorithms considering more than dozen risk factors.
Factors that contribute to the likelihood of threat such as asset reachability, exploitability, active malware campaigns, geography, industry type, and factors that contribute to potential impact like business context, and asset rank are considered to give the most robust risk score for each vulnerability.
Remediation
Remediation is the process of identifying and fixing cyberattacks or vulnerabilities. It is an important part of cybersecurity, as it can help to prevent future attacks and protect data and systems.
Response to identified vulnerabilities through remediation efforts is often considered human resource-intensive and time-intensive. Often tracking of remediation activities is done offline in spreadsheets and is found to be cumbersome by practitioners.
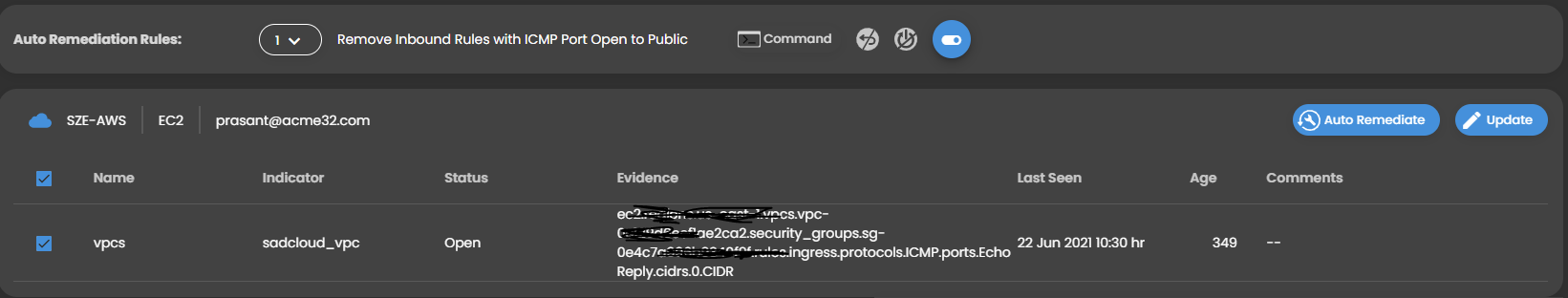
Instead of managing remediation activities in spreadsheets, Seconize DeRisk Centre comes with out-of-box simplified workflows to assign the vulnerabilities to respective stakeholders like Security Analysts, Application Engineers, and IT Administrators with appropriate target dates and notification mechanisms.
This helps Security Managers, and IT Managers track the progress and generate executive reports accordingly.
Single click automated remediation for Cloud misconfigurations brings down the mean-time-to-remediate from weeks to minutes.
Reports
Seconize DeRisk Centre provides out-of-box canned reports in both PDF and CSV formats that can be configured to your inbox. Reports are carefully designed to cater to a variety of needs such as
- Security Posture Assessment Reports that can be shared with external shareholders like Customers, Regulatory Authorities, and Auditors
- Security Posture Improvement Reports that can be shared with C-level executives, Senior Management, Board, and Investors
- Security Posture Management Reports that can be collected as evidence for Compliance and Regulatory audits
- Full spreadsheet exports that can be shared with both in-house and offshore teams.
- Redacted/Minimized spreadsheet exports that can be shared with external stakeholders.
Sample reports can be requested by reaching out to us at hello@seconize.co.
You can learn about how Seconize DeRisk Centre can help you with Asset onboarding, Classification, Continuous Assessments, and Administration in our next blog (Part – 3 of this series).
If you missed Part – 1 of the series, click here.











Recent Comments